Criminology & Globalization:
The Numbers
Game in Global Perspective
With the Crime Phenomenon – Part II
by Professor
Dr. Jacob van der Westhuizen
Professor Dr. Jacob van der Westhuizen is a noted criminologist and the
former director of a major South African criminology research institute; he
currently serves as a Research Consultant to the University of South Africa
where he directs the work of postgraduate students of criminal justice and the
science of asset protection and security control. Dr. van der Westhuizen
received his Bachelor of Arts degree, Bachelor of Arts with honors, Master of
Arts cum laude as well as his Ph.D. degree from the University of South Africa.
He is a member of the International Narcotic Enforcement Officers Association,
the International Police Association, and an Associate Member of the
International Association of Chiefs of Police.
12.0 The origin of global conflict
We shall have to become familiar
with and prepared to accept the fact that we now live in times in which the
nations of the world vie for land, oil, water, food, as well as all other
scarce resources such as gold, diamonds, manganese, copper, iron, wood, and too
many others to mention in this regard. The fact of the matter is that nations
and countries of the world compete
with each other to have unrestricted access to these resources, come hell or
high water, conventional war or terrorism, hardship or calamity.
At this stage it would be appropriate
to track down the epicentre of the global conflict phenomenon and to unscramble
the central point of the driving force within its gigantic body. For this
reason a threat evolvement scale is presented to highlight the major features
and emerging steps that lead up to its highest pinnacle, which is a war driven
by acts of terror and brutal slaying of the masses.
Sometimes such massacres are
disguised as ethic cleansing, bloody revolutions, mop-up operations; or
internal and domestic strive/infighting that should not be interfered with from
outside. However these outrages are put forth as rationalizations for
terrorism, it remains for all to see that these weak excuses are poor efforts
on the part of leaders to absolve themselves by a) pronouncing themselves free
from blame and obligation; b) acquitting themselves from rebuke; c) declaring
themselves not guilty; and d) pardoning or giving themselves absolution for any
sins committed.
12.1 By means of a Threat
Evolvement Scale (TE Scale)
we shall now look at some global security
threats(22
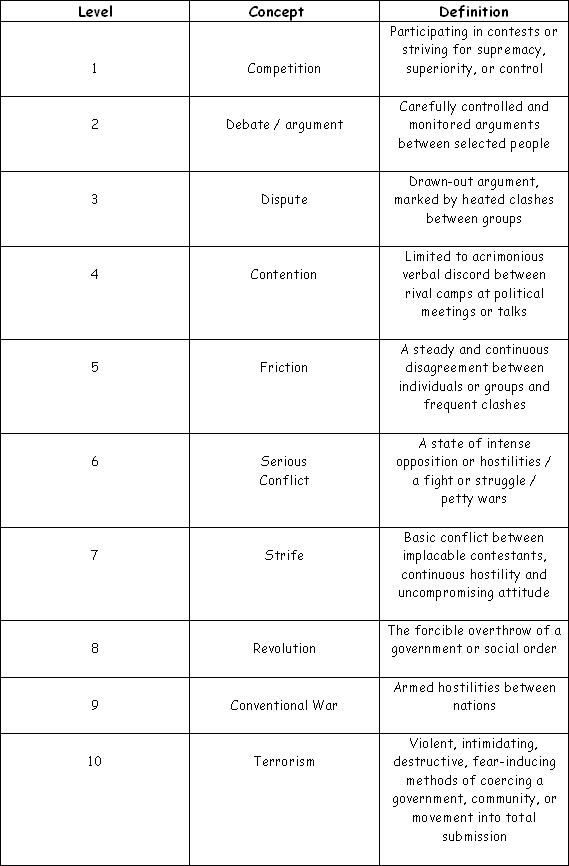
An in-depth look at security threats by means of
a Threat Evolvement Scale (TE Scale)
12.2 Scope
As can be deduced from the table, terrorism is nowadays defined as the highest form of conflict on the TE scale, earning a level 10 position on the evolutionary scale; while competition which occupies the lowest level shows a reading of 1. Between these extremes another eight degrees of escalating conflict as resultants of competition are shown, bringing the total sliding scale effect of conflict from low to high evolvement to ten.
12.3 On the flipside and on the slipside of the coin
Under the heading ‘A World Divided –
In a supposedly borderless era, countries are rushing to wall themselves off
from neighbors’ Simon
Robinson quotes regional Asian leaders who propagate smooth flows of goods,
services, peoples, technologies, knowledge, capital, culture, and ideas. He
points out, however, how the very nations plot back home to separate themselves
from their neighbours by means of concrete walls along their borders. He goes on to say that this phenomenon is not
only confined to the
13.0 Interventions of the numbers game on the national level
13.1
There is a total lack of concentric understanding or application of
home, community, workplace, peer groups, society, and government consensus with
respect to values and norms
Democracy and its bed mate,
capitalism, have ushered in the notion that the Will of the People represents
the highest will and replaces the Will of God. We no longer view the Ten
Commandments as the basic foundation of our legislative powers and the anchor
of morality. A host of other religious beliefs has moved in to demand their
share of the people’s prospects and interests. Concentrically, our
understanding, application, and internalizing of yesteryear values and norms
have fallen by the way.
13.2 Macro transgressions of peace,
prosperity, and security
A very disturbing modern trend is that some nations of the world have come to believe that the scarcity of land, water, raw material, oil, and other commodities can be rectified by redefining the private law that has traditionally recognize legal ownership, proprietary right, right of disposing property, and private defence of property ownership. Various reasons for grabbing, taking, invading, or snatching these prized things from their rightful owners are a given, for example that (i) these elements in the set were stolen from them in the past and they feel nothing for the rights of the current so-called victims; (ii) the poor people of the world have a right to lay a claim to the superfluous riches of the world’s millionaires and billionaires; (iii) globalization is a term invented by the rich, ruling nations of the world in order to submit the poor to further entrapment into poverty and destitute; (iv) the rich people of the world whip up conflict between nations by fabricating evidence that oil-producing countries prepare for a mass-destructive war against them, while the oil countries believe that this is a ploy to attack them and to take possession and control of their prized oil wells; and (v) then again the rich people of the world enhance and propagate the idea of globalization so that their goal of enslaving the ‘stupid’ masses of the world is easily facilitated and achieved. Whatever the verdict, the fact remains however that even some poor nationals resort to invasion of land and homes; grabbing and alienating what do not rightfully belong to them.
On the other hand some of the rulers in the rich countries of the world, who are recognized as the torchbearers of modern civilization, believe that there are factions in some rich and poor countries that plan terrorist acts against them and that these people are extremely dangerous and capable of crippling their countries’ economy, infrastructure, lifestyle and civilization.
It is therefore imperative to closely watch and monitor the intentions and actions of these so-called wildcards and loose canons, especially when there is evidence forthcoming that they are developing nuclear bomb capacities. Over the years many of these beleaguered countries have adopted a zero tolerance approach towards them and have grown to become oversensitive and overprotective of their own belongings.
The upshot of the frenzied conflict is that both sides of the coin, the slip-side and the flip-side, are indistinguishable. It has become quite impossible to tell the one from the other.
13.3
What is wrong with this state of affairs?
Let us say it as it is: we live in a
millennium in which no-one, yes, we repeat, no-one in the wide world has
neither the right to kill other people, nor the licence to maim or humiliate
anyone. Likewise, taking illegal or wrongful possession of another’s land,
property, or house, is offensive, indecent, and criminal.
13.4 What should be done in the first
place?
In stead of destroying tangible values, mankind has to create new values like lawful, proper and regular jobs, viable businesses, and bright opportunities to work and prosper in a free country; devoid of discrimination, as well as racial and other kinds of prejudice. People that destroy a) the lives; b) the limbs; c) the honour; and d) property of others, do it solely to subject and enslave those around them. The destroyers of values suck their direct and indirect victims dry and left them feeling ashamed and guilty, without any will, discipline, dedication, and determination to face the future.
13.5 Why are we playing the waiting game?
Our lethargy and unwillingness to devise strategies and techniques that may prevent and curb the escalating crime problem and the growing demands for war effectively, stem from our acceptance of the current games we are playing. We have grown used to waiting in queues. Apart from our everyday queuing at post offices, banks, shops, and a myriad of other places, we take it for granted to tow the line: a) in police stations to lay complaints; b) over the telephone to report a crime; c) in anguish to hear from the authorities when to appear in court as a witness to a hijacking, burglary, robbery, murder, assault, or other types of violent crimes; and d) in disappointment at anticipating a better protection deal for victims of crime, but waiting in vain to see the light of day.
13.6
The terrible risks we are facing
It would serve no purpose to labour the points about to be made. Each of these issues are currently being displayed in the international arena of thought and afterthought; thus any amount of overemphasis will only dull the consciences of those that are in fortunate positions to prevent, minimize, or to stop their impending impact further. All these abuses and misuses ought to be classified as criminal acts that call for harsh punishment.
14.0 Quantification of measurement and
prediction of threats
It is not easy to identify and quantify the different elements of the threat phenomenon. For one thing: there are too many unknowns; and for another: there is no assurance that the currently-available forecasting methodology comes up to scientific standards of validity, reliability, sensitivity, communication, utility, and immediacy of response and reaction.
14.1 A new approach
We are obliged to adopt a new
approach in order to meet the demands of the new millennium and all its
subsequent ramifications in respect of unexpected changes.
First of all we need to launch a new
scientific discipline which supplements that of criminology. Secondly, we need
to identify an additional study object that highlights the crime phenomenon, a
move that would enable us to come up with valid and reliable solutions to
pressing issues such as insecurity, uncertainty, and hopelessness. The crime concept
covers such a large and varied array of illegal acts that it confronts the
researcher with the inevitable and hopeless task of walking with kings while
keeping the common touch.
Just now we need an complementary
study object that would allow us to focus our energy and efforts on making the
world a better place to live in; firstly by doing away with criminal justice
procedures by substituting them with streamlined, unadulterated,
simple-to-the-point steps that allow us to arrest, arraign, and punish culprits
speedily and effectively. Our second bid is to eradicate all institutions,
systems, and laws that are obsolete and past their shelve life. Third in
contention is victim as well as offender vulnerability analyses with a view to
prevent or eradicate global wars and subsequent transgression of humane values
and norms.(24
Next we consider vulnerability equations of
the first and second kind in order to come to grips with the victim’s as well
as the criminal’s mindset(25
14.2
Formulating a victim vulnerability equation
of the first kind
Our present quest is to formulate a vulnerability equation of the first kind.
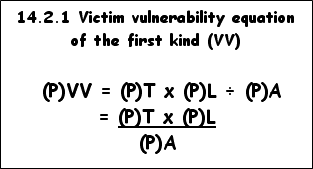
In our bid to come up with an effective first and second floor equation to gauge the vulnerability of persons to crime, we can spot three things that all floors of our victimization control building have in common: a) the threats of victimization (T) are more or less the same, but vary only in respect of seriousness, content, and application; b) the backlog in preventive, subduing, and controlling measures (L) include all those measures that can be applied on the ground floor as well as new tactics and strategies on a grand scale which comprise each and every individual, the whole family, the entire community, and the society at large; and c) the degree of security awareness (A) covers a wider range, encompassing everyone in sight, but focusing on the collective will and goodwill of our leaders and authorities as well as those institutions (such as governmental and non-governmental departments and organizations) that must make it their business to set the pace and to get involved in crime control.
14.3 Formulating a victim vulnerability
equation of the second kind
On the assumption that a victim vulnerability equation of the second kind features the same factors as the equation of the first kind, but calling for more detail and in-depth probing than its predecessor, we may as well use the very same first edition equation, on condition that we add a superscript plus sign (+) to each factor as follows:
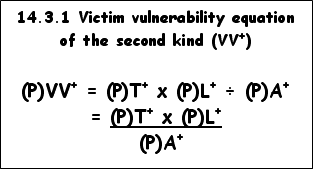
This victim vulnerability equation of the second kind can be utilized to let us know how vulnerable we are in our country, by gauging the following determinants of would-be victims’ vulnerability to victimization:
(a) the collective threat of criminalization to which the population at large is exposed (for example faction fighting, murder, assault, kidnapping, fraud, hijacking, robbery, theft, rape, child molesting, child negligence, pornography, drug addiction, war, revolution. and other vices);
(b) lack or absence of effective authoritative leadership qualities, capacity, will, and determination to prevent and curb victimization (for example periodic failure to (i) publicly denounce and condemn all crime and victimization; (ii) pass legislation to punish and rehabilitate the guilty offender properly; and/or (iii) spruce up the administration of justice, i.e. legislation bodies and departments, the police service, the courts, and the prisons); and
(c)
lack or absence of a collective security consciousness or awareness, which
translates into (i) a want for positive leadership and exemplary affirmative
action (for example: ‘I express my utter disapproval of rape and my
government’s unequivocal rejection of the victimization of women and children;
therefore we see to it that this type of offender is hunted down and punished
with the full legal impact and might of the law); (ii) the need for better
legislation, understanding and compassion with the victims of crime, and their
need for victim compensation and damage control; (iii) the demand for effective
policing and community protection to guarantee the privacy of hearth and home;
and (iv) the need to forcefully address official and private corruption and
bribery.
14.4 Propensity for criminal behavior
We are now taking a new coin in hand to look at the propensity of a human being for criminal behavior.
The first crucial consideration is to re-define the concepts crime and criminal victimization in order to open the correct doors which could lead us to valid and reliable answers.
14.5 Revisiting the crime definition
From the discussions meeting our latest requirements, we define crime as natural rule-of-law do’s and don’ts (legal prescriptions and proscriptions) willed and determined consensually by societies at large to maintain, restore, and stabilize peace and order in a country. However, the concepts crime and criminal victimization differ from each other in respect of their scope.
The scope of crime is much larger than the scope of criminal victimization. Many crimes, such as those comprising no injured person and also no specific person at all, can be regarded as victimless crimes. Examples include a) the use and abuse of drugs, accidentally picked up by a group of teenagers; b) the reckless driving of a motor vehicle on a public road, despite the fact that the driver has not caused any accidents; and c) being caught in possession of or in the act of smuggling, importing or exporting contraband.
A rule of thumb is to regard any crime as being a victimless crime when it is seemingly impossible to pinpoint the injured party and to identify the direct victim; or to establish mens rea (guilty mind; wrongful intent; criminal purpose or intention – ream linguam non facit nisi mens rea )(26
14.6
Defining criminal victimization analytically(27
Criminal victimization is the targeting of a person or persons for illegal spiritual, social, physical, and/or material/economic gain:
a) general exploitation (of the victim): misuse, abuse, manipulation, duping, swindling, defrauding, persecuting, stalking, tormenting, deceiving, hoodwinking, tricking, outsmarting, causing harm and injury, dishonoring, robbing, maiming, and killing;
b) psycho-somatic need satisfaction (of self):
examples are (i) theft of food to satisfy the normal hunger need; (ii) perverse
sexual need satisfaction by breaking into homes to experience new, exciting and
blood-curling adventures; and (iii) other abnormal need satisfaction behavior
and stimulation of fancies such as to get orgasmic relief when a window is
smashed during a burglary or when a building is set on fire.(28 Bromberg, W. 1965. Crime and the mind. MacMillan:
c) focused financial need satisfaction (of self): for example when (i) homes, businesses, shops, banks, and churches are robbed for cash or goods that can be sold for ready cash; (ii) pedestrians are robbed of their cash to enable the thief to buy drugs or settle his drug account or outstanding loan; and (iii) cars are hijacked on order from crime syndicates or for their scarce parts; and
d) satisfaction of group needs and/or obeying commands of leaders: in order to show loyalty and concurrence with group values and norms by breaching societal laws and/or family and community rules and regulations; as well as committing crimes to cover up other crimes that have been committed previously.
14.7 How vulnerable is the predator?
In order to use the predator as a general exemplar of a criminal that preys on his victims in one or more of the various ways mentioned supra, we must now assume that he or she likewise satisfies the conditions for victimization and vulnerability analyses of law-abiding citizens, in the sense that they have been ‘victimized’ and ‘enslaved’ from birth onwards by built-in genotypic and phenotypic traits and characteristics, as well as crucial mind-bending experiences that they might have gone through.
Our male predator is, however, unique in looks, character, mindset, background, thoughts, feelings, emotional drives, psychosomatic and other needs, and motivation. We use him as an exemplar only for demonstration purposes.
14.8 What is the likelihood that our
predator would be affected by built- in genotypic and phenotypic traits and
characteristics, and crucial mind-bending experiences?(29
This all-important question will have to remain unanswered until valid, reliable research has been undertaken. For now, we know that Eysenck’s propounded theory of an individual’s inability to get conditioned to values and norms may assist the researcher in resolving the issue at the phenotypic level.
In the meantime, for argument’s sake, we can assume that a variety of other environmental influences can make a direct and indirect impact on our predator’s personality, character, lifestyle, mindset, health, and motivation. Chief among these are the influence and authority of his family, friends, peers, community members, co-workers, societal kingpins, pace-setters, and trend-setters. Thus we refer to him as a ‘casualty of cavitations’ – (i.e. he suffers a lack or absence of socialization because of a formation of a cavity in his personality structure or of a vacuum in his character, caused either by genetically-inherited traits and/or environmentally-acquired characteristics).
We are now in a position to state the following premises :(30 (Jacob p. 123.) a) the predator is (i) a casualty of cavitations, one who suffers from a poorly-developed genotype that spawns an equally-poor phenotype; i.e. an individual who does not have a strong enough superego nor built-in brakes that can be slammed on before he clashes with his parents, community, the police, authorities, and the society at large; (ii) on the eve (and at the receiving end) of a string of judicial proceedings against him, such as detection, arrest, prosecution, conviction, punishment, imprisonment, labeling, harassment, persecution, and rejection; and (iii) exposed to bad influences of peer groups, friends, and adults who use and abuse him for a number of questionable reasons;
b) the predator finds it hard and/or impossible to call or fall back on the same law-abiding mechanisms as the run-of-the-mill kid on the block, such as his parent’s love, guidance and affection, his siblings’ support, his peer group’s understanding, and the patience and sympathy of his community leaders; and
c) to stay afloat and out of trouble, the predator must resolve a large number of personal, familial, and peer group dilemmas: thus he lands up in dilemmas that call for free-will choices between good and bad, right and wrong, and suchlike (whatever his definitions of these concepts are at that moment).
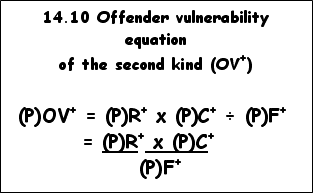
Offender vulnerability is thus a function of three independent factors: a) retarded genotypic and phenotypic development (R); b) community intervention (C)); and c) free-will intervention by the offender on his own behalf (F).
We have now reached a stage where we can formulate offender vulnerability of the first kind (OV) as follows:
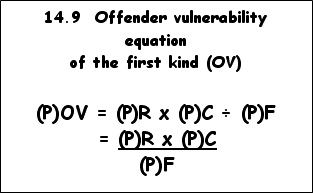
As can be deduced from the formula above the factors that threaten to demolish the offender’s future are given as
while the most effective neutralizing factor seems to be the offender himself [(P)F], namely the acceptance of his defeat and the generation of a will and determination to turn over a new leaf. If he is not prepared, willing and able to do this, his road ahead will once again be turned into a race against the tracker dogs.
The offender’s road through the police cells, the courts and the prisons and his life as a recidivist, have changed and tremendously upset his chances to calm down to a law-abiding existence. He is no longer in a favorable position to appeal for community support, and the sympathy and goodwill of the very people he has betrayed and shamed. His R-factor is now cast in the very stones of his prison walls, while his C-factor is slowly but surely turning into drying cement walls of rejection. Thus he faces and feels the hard and fast rules of man: no more concessions, no more leniencies, no more indulgence; but only the sweat between a rock and a hard place. Once again his fate is in his own hands. He has to his disposal the F-factor to rescue him from a lifetime of misery, simply by pulling himself up by his own bootstraps – his only remaining lifeline.
14.11
Links in a chain of criminal victimization(31
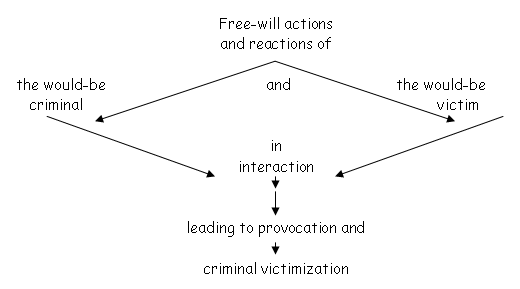
Any intervention to curtail or stop a causal fuse from igniting a crime is restricted to the five links mentioned above. The free-will actions and reactions of the players – considered separately or in concert – may provoke conflict that translates into the criminal behavior of any one of the actors, or both of them at the same time.
14.12 Would-be victims and would-be
criminals in interaction(32 JvdW ibid
The first two links in the chain of victimization spark off much speculation about the viability of instituting victimization control measures after the fact; casting serious doubt on the role of society at large to invert or to reverse the deviant tendencies and inclinations that have been strongly-conditioned into the phenotypic mindset of the criminal. It comes as no surprise that the general recidivism rate is more or less fixed at the two-third level annually.
It seems that we have to contend with a two-legged beast here: on the one hand with the threat of a hardcore, stunted, professional criminal; and on the other with an emotional, highly-strung, and ready-to-explode individual.
Would-be victims and would-be criminals in interaction present one of the toughest issues to describe, explain, predict, and prevent. No amount of energy, money, time, and effort can reveal the whole, exact and reliable truth about the inner relations, anticipation, conflict, anguish, disappointment, fear, shattered hopes, and sorrow of the interacting players. No amount of introspection can afterwards uncover the real essence of the drama that has unfolded in the wake of a fatal confrontation.
The bottom line is here for all to see: we cannot, and are not potentially capable of predicting and controlling all hum
an behavior, no matter how hard we endeavor to do so. That is a given.
14.13 Free-will actions and reactions of the
would-be victim and free-will actions and reactions of the would-be criminal(33 p.188
Many open and/or subtle attempts are usually made at curtailing, altering, restricting, or constraining free-will actions and reactions that are harmful to individuals, families, commercial groups, communities, societies, and crowds.
14.13.1
Constraints of the first kind
Notably among the official reactions to crime are formal constraints such as laws, ordinances, regulations, and rules that are (i) proscriptive: a) banning or exiling an offender; b) rejecting or denouncing a practice as dangerous and harmful to others; and/or c) putting a person outside the protection of the law; and (ii) prescriptive: laying down of specific authoritarian and customary do’s and don’ts which forbid certain actions and reactions, all of which are punishable by law.
14.13.2 Constraints of the second kind
Cultural, social, and economic constraints comprise taboos on actions and reactions that are a) frowned upon and disliked by others (for example the breaking of protocol or etiquette standards); b) rejected as unfit and below a decent civil standard (for example farting in public places); or c) defined as just short of constituting an infringement of the law (for example short-changing a customer at the cash register).
14.13.3 Despite constraints, they
talk-the-talk and walk-the-walk
Evidence accumulated over the years show that these two kinds of constraints do not deter the players in violent dramas to talk-the-talk and walk-the-walk right past and beyond the point of no return. Committers of violent and other serious crimes do not keep the threat of punishment in mind before the fact, but heed only the pleasure of satisfying some or other need at that very moment. They can be labeled practical hedonists – persons who are oblivious of the punishment and pain that may follow after the fact.
In reality, there is nothing the authorities or society at large can do to stop the criminal from flying off on a tangent. No outside intervention or threat of punishment can deter the murderer, rapist, assaulter, fraudster, kidnapper, and robber from committing his or her dastardly act or to refrain from reacting fiercely when confronted or provoked into retaliation.
Even before committing trivial, petty, or non-serious crimes, a person will, nine times out of ten, give no thought whatsoever to punishment, or made any effort to calculate the likelihood of being discovered or apprehended.
14.13.4 Worthy of note: a ‘no tolerance’ approach
What seemed to have produced some results worthy of note was the New York Police’s ‘no tolerance’ policy (also referred to as ‘a zero-tolerance’ or ‘the broken window approach’) towards the end of the last century – a theory that necessitated the prosecution and punishment of all offenders across the board, from the most trivial through to the most serious.
In essence it boiled down to educating the public at large to develop a caring, law-abiding awareness and a culture of abstention and restraint from criminal behavior and offending habits – one that could hopefully override the laissez-faire spirit which had pervaded the actions and reactions of the public at large at the time.
14.13.5 Real-life aversion therapy
The introduction and relentless continuation of a real-life aversion therapy like the above-mentioned ‘no tolerance’ prosecution-and-punishment policing policy, call for a judicial system that has the capacity, toleration, will, and determination to apply the system dispassionately, smartly, stringently, and unflaggingly. Any voids in the functional execution of duties or gaps in the structural armor of the administrators of justice may spark off renewed efforts by the public to beat the system.
15.0 Role of the powers that be to help resolve
certain areas of concern
The powers that be more often than not play decisive parts in helping to secure certain public and private areas of concern, especially in that they focus on and zoom in on the most important issues being addressed and tackled, such as among others the above-mentioned demand-and-supply forces.
16.0 The role of the Numbers Game in
Research Enquiries
We are obliged to step up our efforts to come to grips with ALL the issues mentioned above, including these which are highlighted below; as well as those that might come to our attention in the days, months and years ahead. It is high time to realize that we are responsible for the speedy and efficient resolution of the imminent threats at our door stairs and that we neither have a place nor the time to hide from their destructive modes.
Below the numbers game is brought in perspective with some unresolved issues in security science, id est., the quest by Ruth Cavan to condense all the different crimes which occurred in the American law books in the fifties and sixties of the past century into a normal distribution curve. This effort at quantifying the myriad of crimes into a distribution that lends itself to calculate central and dispersing values as well as enabling a researcher to use the information to explain, predict, or put forth suggestions for the control of the crime phenomenon. Apart from opening up these valuable opportunities to witness the global tendencies of growth, decrease, or stabilization of the crime phenomenon, the Cavan technique would have enabled the Police to enforce law and order most effectively.
16.1
Effectiveness (E) = Quality (Q) X Acceptance (A)
This formula(35 tells us that the effectiveness of policing is a function of two independent variables: the quality or efficiency of the policing action and reaction (including the care and diligence of the officers to conduct their service duties smartly and decently towards the everybody at large); and the acceptance of the policing input by everyone involved : (colleagues, alleged victims, eyewitnesses, the public at large, authorities, and suspects, whether arrested, undetected, or still on the run).
Below
is a portrayal of a normal distribution of crimes according to Ruth Cavan(36
16.2
The Criminal Numbers Game in perspective with a normal distribution of crimes according
to Ruth Cavan(37
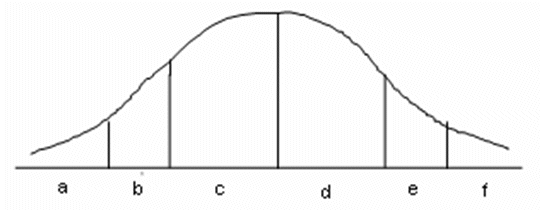
16.3 Ruth
Cavan notes that judicial
intervention makes a precise, absolute distinction between criminal and
non-criminal behaviour. She maintains, however, that the societal definition of
(i) what constitutes crime; and (ii) what should be tolerated and what should
be condemned, is far more potent than the legal definition. Thus the public at
large will tolerate certain crimes despite legal prohibitions or
commandments. Her 1962 study, among many
others, generated the criteria for behaviour as portrayed above on a normal
distribution curve.
A = the criminal underworld (absolutely condemned by society)
B = extremely poor conformity to the law (strongly condemned)
C = slight negative deviation from norms (condemned but tolerated)
D = average conformity (sporadic condonation and/or approval of trivial
offences)
E = slight positive deviation (tolerated but not approved)
F = extremely strict conformity to the law (excessive and blind adherence
to the letter of the law is condemned)
G = ideological counter-culture: organised political, social or religious
groups (pose a real threat to conformity)
Although this model has some defects, it
nevertheless enables us to explain society’s potential for defining behaviour
as lawful or unlawful and its reaction to crime.
Some of the most prominent defects which
can be discovered here are briefly discussed below.
(i) Cavan refrained from pointing
out that her model represents but one possible distribution of crimes across
the board. As a matter of fact we may encounter other kind of distributions in
other countries, such as Poisson or Chi-square dispersions.
(ii) Her own proposed ‘normal’ distribution
becomes a bi-modal dispersion model because she resorts to an ideological
counter-culture defined as ‘organised political, social or religious groups which
pose a real threat to conformity’.
(iii) The three defining factors, that are
supposed to validate the curve as a universal description of man’s illegal
behaviour in societies where a) the rule of law, b) democracy, and c)
capitalism reign supreme, are not applicable in most countries of the world;
and if applicable, not always valid because of differential relevance in
respect of functioning, dedication and commitment. It is certainly not
portrayals that are in general true to life on earth or reliable in terms of
statistical significance.
(iv) Although Cavan’s “average” criminal is true
to life and provide us with new knowledge and insight about the
man-in-the-street’s definition of white collar crime, the other categories are
sterile and devoid of any real substance: they are just specifications.
(v) Despite Cavan’s assertion that her curve
enables us to work with central and dispersion values, there is no evidential
proof available to validate her claim.
(vi) Cavan’s legal definition of crime has no
comparative counterpart in appearance and function; therefore it does not qualify
as a valid and reliable descriptive tool in science. Cavan tried to remedy this
gap later on but did not succeed in convincing her contemporaries to accept her
beliefs.
16.4 A final verdict
Whatever the criticism levelled at Cavan’s
efforts to normalize breaches of the criminal law, the fact remains that she opened
up an avenue upon which researchers may venture forth to show definitively that
a refined definition of crime that lends itself to quantification, can be
dispersed on a normal continuum of variation, featuring the incidence of homo criminalis on the one hand and homo nobilis on the other, with the
distinction that between these opposites many degrees of differences are in
evidence.
Next a very brief discussion follows in order to account for the numbers game which is played out in the judicial systems of western-oriented societies.
17.0 Punishment put in perspective with modern-day practice of the
numbers game
There is very little of value to be
added to Vold’s brilliant analysis of punishment in his book Theoretical Criminology.(38
Running the risk of not doing full
justice to his thoughts on punishment, I have nevertheless decided to reflect
his thoughts in a brief summary with the request that those readers who want to
delve deeper into his words of wisdom, should make it their business to get
hold of the book. However, I have felt obliged to have left out some of his
obsolete ideas and to have substituted my own. .
17.1 Contradiction in ideas and attitude
Vold contends that ‘many present-day
problems in penology grow out of or are extensions of the basic contradiction
in ideas and in attitude’ when punishment
and/or treatment is considered as a
panacea for crime.
17.2 The infliction of punishment
Punishment is inflicted by design,
not by accident. If aids are contracted by the offender during a rape, it is
not considered to be part or parcel of the punishment lay on by the court and
executed by the authorities in question.
17.3 Punishment versus treatment
Punishment is a form of societal
reaction to crime and dates as far back in the history of man as part of his
living memory: probably as the only response to acts of terror, murder,
forcible rape, assault to cause grievous bodily harm, abduction, and
hostage-taking; more than likely as a suitable panacea which incorporated all
the various motivations to punish the offender, such as retaliation,
deterrence, and reparation. There is some strong evidence that religion and
faith played a decisive role in perpetuating its practice, especially when
serious crimes were committed. This concludes Vold’s views on crime and
punishment in his book Theoretical
Criminology.
18.0 Various other topics in respect of crime and punishment discussed
by the author of this article
18.1 Treatment versus punishment
The term ‘treatment’ has been
borrowed and adopted by penologists from medicine. This analogy implies that
criminals are ‘sick’ people, not to be punished, but to be treated instead. It
also means that the ‘causes’ of crime (e.g. ‘psychopathy’ ) can be discovered
and corrected through intervention.
18.2 Rehabilitation of the inmate
Classification of prison inmates in
groupings such as nature of offence, age, sex, race, and gross mental condition
is well-tried in western-oriented countries, but also violated because of gross
overcrowding. Rehabilitation of inmates is done sporadically and receives no
100% favourable response from neither the officials in charge of the
proceedings, nor the inmates who either adopt a submissive attitude of
‘I-am-doing-time-so-get-it-over-with’ or a
‘I’m-playing-along-in-order-to-get-the-maximum-benefits-from-the-system’. No
wonder that the overall recidivism (relapse into crime) rate is round about 70%
in most of the prisons world wide.
18.3 Incarceration as a form of punishment
Imprisonment of convicts should be
understood as being milder and more humane than corporal punishment or the
death penalty. That is the ideal, the practice tells the modern researcher
another story, one of hardship, humiliation, immobilization, banishment,
beating, whipping, mutilation, and suffering imposed behind the high walls of
the prison, deliberately by the prison officials, and practically as a result
of overcrowding and aids contagion. The abolishment of the death penalty in
many, but not all countries of the world, signifies a welcome change, but
unfortunately no permanent walk in the park.
18.4 Historical perspective on crimes and punishments
over the ages
The outstanding things that have come
to our attention during this enquiry boil down to the following propositions:
r Fear of consequences of crime and violence
abounds
r Calling on mystical powers to come to the
assistance of the authorities is rife
r Overreaction, using sledgehammers to kill
flies is the norm
r Uncertainty in respect of definitions of
situations, role of police, and the role of parents is conspicuously widespread
r Relativity of crime definitions and
punishments are of common occurrence
r No amount of significant conditioning and
learning from past experience are noticeable
r Apart from shifting earth, all-out efforts to
shift people’s mindsets remain the most difficult task to perform successfully
on planet earth
r Past maxims and sayings have become obsolete,
for example: crime does not pay, about one third of all people are born
criminals, and one cannot reform or rehabilitate a criminal, and so forth.
19.0 How the numbers game is being played by
the world at large(39
Regular scrutiny of newspapers, and watching the news broadcasts, are apt to reveal that the nations of the earth have their own agendas, motivated plans, purposes, and goals to attend to, with the inevitable result that they lay down their own rules, targets, objectives and aspirations.
The current trendsetters and opinion leaders are apt to sponsor and propagate the western ideology as embodied in democracy, capitalism, and the rule of law; known for short as the decapirul model.
A very alarming result of this is that this exemplary pattern is sometimes not accepted voluntary, but rejected on command, whereupon war inexorably follows. The argument in favor of the decapirul model is briefly that the model can be used and abused by developing countries in that they employ the model only to get voted into the driving seats, whereupon they fashion the system to suite their own agendas and needs afterwards. A few years before Christ the Greeks had a word or two for the adoption and implementation of the democracy poling system: they call it the tyranny of the masses(40. And this seems to reiterate another old saying that goes: ‘Different strokes for different folks’.
The bottom-line definition of the numbers game reiterates that it is not so much a game of chance; but in realty terms, a game of skill and manipulation rolled into one.
That brings us to a brief exposition of game theory, a theoretical game developed and employed by the Allied Powers to gauge the strategic and tactical moves on the war map of the enemy and to plan accordingly to defeat or neutralize any future threats and onslaughts.
19.1 The quest for theory and methodology in science
Any introduction to
a science requires some indication and guidelines in respect of a substructure
of theories that can account for feasible explanations of its research subject
as well as its research methodology which are meant to highlight its approach,
methodology, techniques and game plan. The games we play in science require
among other things some reference and explanation of game theory, an
approach and methodology that are introduced below.(41
The reason for this
choice stems from the notion that our security options are prioritised by the
calculation and implementation of acceptable levels of survival chances and the
expectation of minimum loss of assets.
19.2 Game theory suggests a problem-solving technique in the games we
play to safeguard ourselves against attacks
We now turn to game
theory to discover why we may be in a better position to make the correct
decision in cases where an attack is launched on us and we have no other choice
than to defend ourselves. It can be shown that game theory may present the best
problem-solving technique possible if Player A (the victim) is able, willing
and ready to exercise three choices, while he (the victim) has rigged up a
security and safety system that leaves the predator with only two choices. With
this in mind the victim devises a pay-off matrix which portrays the optional
moves or choices that could be made by both of the players.
19.2.1 Rationale for problem
solving with the aid of game theory
When game theory is applied in security and safety matters, it is
performed on paper or in the head of the would-be victim in order to: a)
establish the best contingency tactics or strategies at the time for the
accosted victim; b) gauge the best tactics and strategies the predator is apt
to follow; c) determine the value of the game for the predator; and d) make a
contribution to the timely identification of soft targets and encourage the
victim to toughen vulnerable chinks in his armor.
19.2.2 The victim draws up a
pay-off matrix
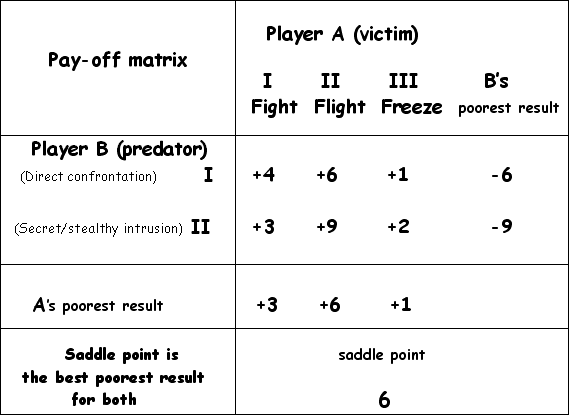
Player A (the victim) confronts a
predator (B) in his home. A’s self-defense applies to any action or reaction
that may result in stopping or forestalling any illegal action and illegal
reaction of B by any legal or
acceptable means. A can
execute three typical actions as portrayed below.
19.2.2.1 A’s options during a direct confrontation with B
I.
Fight
back in order to neutralize B’s
attack. A regards himself as
a total
loser in a direct confrontation with B.
II.
Take
flight and hide in sleeping quarters; thus avoiding any further risk
of suffering loss of life,
limb, or honor. Loss of property is covered by
insurance.
III. Freeze and remain immobile as if paralyzed from fear.
19.2.2.2 A’s options during a
secret, stealthy intrusion by B
I.
A does not attempt to neutralize B’s
attack. A regards himself as a
likely loser during a
secretive, stealthy invasion of his home.
II.
Take flight long before the invasion is
done and hide elsewhere; thus avoiding any further risk of suffering loss of
life, limb, or honor. Loss of property is covered by insurance. A has the opportunity to alert
the police, his alarm company, and his neighbors for help.
III.
Freeze
and remain immobile as if paralyzed from fear.
B’s options: choosing either a direct confrontation with the victim,
or a stealthy, secretive invasion into his home
I.
Accost A
head-on. B’s poorest result is -6.
II.
Steer clear of A. B’s poorest result is -9.
The best poor result in the set of poor results is -6, therefore B will always play his I, and
never his II; he opts for the lesser evil.
19.3 A’s decision on the
strength of the results portrayed in the pay-off matrix
A will always play
II and never I or III, opting for the best advantage.
19.4 B’s decision on the
strength of the results portrayed in the pay-off matrix
B will always play I
and never II.
20.0 Saddle points indicate pure strategies
The least complicated type of game is one in which the best strategy
for each player is a pure strategy. This type of strategy is obtained when the
pay-off matrix has a saddle point as reflected in the pay-off matrix above.
Here the value of the game is 6.
By repeatedly following his strategy II A ensures that he wins at least 6 units. When B plays his I A gains 4 units and when B plays his II A gains 9 units. B has therefore no other choice
than to follow his I.
The implication for security is that every route an attacker follows to
reach the target, must be evaluated and appraised with a view to game theory
analysis and subsequent hardening. For A
the best strategy is here indicated by the saddle point, 6.
20.1 A
list of other routes to be considered for analysis
1.
Hours
of the day/ days of the week/ months of the year/ seasons of the year during
which predators are apt to strike
2.
Type of
home or homestead predators prefer to burgle
3.
Type of
environment/ suburban/ business/ street/ town/ farm/ smallholding predators are
sure to target
4.
Type of
security and safety set-up predators select to penetrate
5.
Type of
car/ vehicle on the shopping list of the syndicate
6.
Type of
victim they prefer to visit.
Please note that these factors are indicative and by no means
exhaustive.
20.2 How to handle
unpredictable behavior
We will now see how a situation can be defined in security science if
there is no saddle point, a case in point where it is impossible to predict the
behavior of the players. For the purpose of this exercise it is assumed that
the players use mixed strategies to increase their average gains. They thus
take rational decisions and we can therefore attempt to estimate the
probability of a decision and the outcome of the battle.
As an example the following
pay-off matrix is constructed.
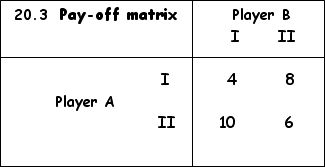
The probability according to which player A chooses his strategy I will now be set at p and that of his strategy II at 1-p.
r
We
shall now proceed to answer the question: ‘What is the best value of p as seen from the viewpoint of player A?’
–
if
player B plays his strategy I,
player A’s gains (G1)
will be:
G1 = 4p + 10 (1-p)
= 4p + 10 – 10p
= 10 – 6p
– if player B plays his strategy II, player A’s gains (G2) will be:
G2 = 8p + 6 (1-p)
= 8p + 6 – 6p
= 2p + 6
–
we now
find the value of p by making the two G values equal to each
other:
2p + 6
= 10 – 6p
8p
= 4
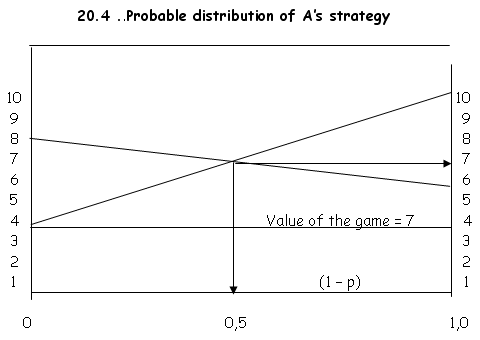
p = ½
and 1 – p = ½
–
we now
answer the question with regard to player’s B’s probable choices in the same way, id est. by equalizing his
strategies I and II:
4q + 8(1-q) = 10q + 6(1-q)
4q + 8 -8q = 10q + 6 – 6q
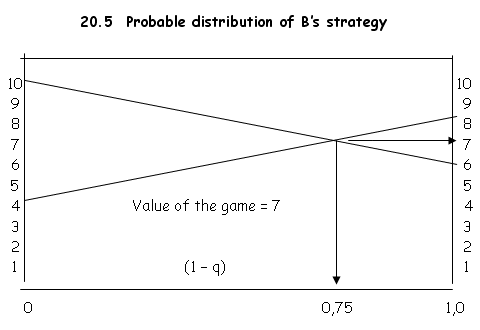
-8q = -2
q = ¼
The value of the game can be found graphically as illustrated below:
r
A
formula, according to which the value of the game can be calculated, is given
in another example below.
20.6 Security problems at Pendulum
We shall now look at security problems at Pendulum, a citrus farm in
the low veldt and see how game theory can be used to improve its security.
Pendulum has two security areas: a business area (B) and a residential area (R). B is worth twice as much as R; and Pendulum can only successfully
defend one of these areas at a time. Maxim is a terrorist group that can
annihilate any unprotected area, but is known to tackle one area at a time.
Since Pendulum has learnt that Maxim is going to launch an attack, it must come
up with a suitable defense strategy without delay.
20.7 Proposed solution of the security
problem
Utility
units allocated
1.
The
value of the residential area is one utility unit
2.
The
value of the business area is two utility units
3.
If both
areas survive Pendulum loses nothing
4.
If the
residential area survives, Pendulum loses
two utility units
5.
If the
business area survives, Pendulum loses
one utility unit.
20.8 Assumptions in zero-sum game
1.
Maxim
is intelligent and cunning
2.
Murphy’s
law dominates the scene of the battle
3.
The minimum
criterion for optimality is that both Maxim and Pendulum after reflection, will choose the lesser of two evils or
the best anticipated end result.
20.9 Proposed solution
1.
Find
the best strategies for Maxim and Pendulum
2.
Calculate
the value of the game, which is Pendulum’s
anticipated advantage.
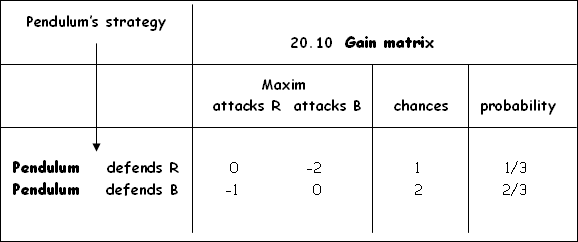
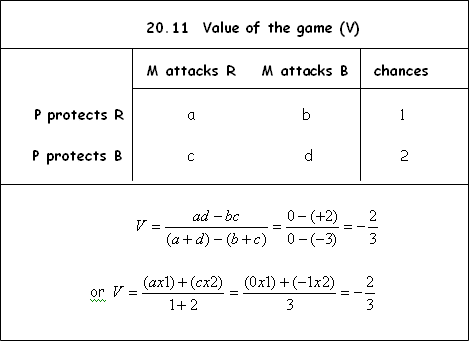
r
The best strategies for Pendulum and
Maxim are not pure strategies since there is no saddle point; there is no value
which is simultaneously both the smallest value in the row and the largest
value in the column.
r
The best strategies for Pendulum and
Maxim are mixed strategies.
r
The probability according to which Pendulum’s plan of
action should be drawn up is: strategy I: P = 0.33 and Strategy II: P = 0.67.
Residential area and business area security are combined with chances of 1:2. For each residential area patrol undertaken, there must be two business area patrols.
21.0 Constraint
theory (CS)42
The formulation rationale of the CS by the author, is to describe and explain the restraints imposed upon human behavior (with or without criminal intent) in regard to the numbers game we play in an individual or global setting, in order to satisfy our specific and overall needs, requirements, and obligations; as well as giving us the scope and focus to evaluate and assess our input.
Here we become aware of the fact that nations, societies, communities, families, and various other kinds of groups have for different reasons subjected selected individuals and groups of people to stringent do’s and don’ts for example to legal restrictions, prescriptions, and proscriptions; as well as a myriad other restraints, ranging from prescribed standards, for example in respect of age restrictions, or unwanted behavior patterns, which may fluctuate in rejection intensity from worrisome to prohibited nauseous acts.
However, we also become aware of the fact that the hunter has become the hunted, in the sense that every authoritative decree, law, or limitation is subjected to the inevitable consequence of inclusive application, in other words, what is good for the geese, is good for the gander. In addition there is also an understanding that the limits of decency, fairness, and civility shall never be violated in the process of law enforcement and law maintenance, despite the probability and possibility of strikes, collusion, uprising, revolution and other means of dethroning the status quo.
In order to put constraint theory in proper perspective with reality, we shall have to break its scope down into an essential number of relative positions, importance and size, such as constraints imposed on the victim and perpetrator of crime; the research officer at work, battling to make sense of issues at hand; as well as externally imposed restraints laid on by natural powers and/or the powers that be.
22.0
Constraint theory put in individual perspective
22.1 Victims or would-be victims of crime
As shown supra the violation of the rights and security of law-abiding citizens is a function of three independent variables: a) the criminal act itself; b) lack of security measures that should have been instituted or adopted by the victim to have warded off attacks and decrease the opportunity of the criminal to have succeeded in causing dead loss; and c) the security awareness of the person or group in question which may enable them to be vigilant and wide awake to spot emerging attacks or illegal acts. These variables impose severe restraints and stress on the victim and would-be victim of crime.
22.2 The perpetrator of crime
The criminal does not escape the hazards wrought by the constraint theory. His or her actions and misbehavior are severely censured and judged by the authorities and the public at large. Whenever the wheels of justice are set into motion, it does not stop until a verdict of guilty as charged or a dismissal is reached. What is extra bothersome is that labeling of the law violator is also done in addition and confirmed by the court of public opinion in the media at large.
23.0
Constraint theory and research
23.1 Restraints imposed externally by authorities and natural sources
It comes as no surprise that any research that touches a sensitive nerve may sometimes be censured by the government denying the researcher any access to data that may work up a storm or embarrass the officials concerned.
Apart from this, natural occurrences such as climatic changes, weather patterns, and environmental hazards may render data gathering in remote areas difficult and sometimes impossible.
23.2 Restraints imposed externally by other sources
Other sources of restraint may occur as part and parcel of interviewing respondents in far away places and experiencing transport breakdowns, motoring troubles, or other types of troubles. It is not too farfetched to expect the law of built-in obsolescence to play an overriding role when least expected, causing for example an engine gasket blow-out; or a total collapse of a hard drive of the research officer’s laptop.
23.3 Restraints imposed internally as a consequence of technological
ignorance, misunderstandings, and inexperience
Quite a number of restraints are self imposed, brought on and about by sheer innocence, ignorance, negligence, or lack of know how. Thus problems may crop up with biased samples, invalid variables, and unreliable observations, to mention but a few; not to forget the propensity to choose the wrong test statistics when responses are measured up for significant differences.
24.0 Constraint theory in global perspective
Last but not least, in fact a bottom line of overriding concern in comprehending the real objectives and nature of the globalization process being driven nowadays is the fact that constraint theory shows up unexpectedly in various guises, places, and time frames. We are therefore obliged to put it in a broad global perspective in order to showcase the meaning of its presence and the reason for its generative power base apparently being constructed with deadly precision and dogged determination in order to define, describe, explain, predict, and control the destiny, fate, and fortune of mankind, a step that should be embraced wholeheartedly by every member of mankind on earth – a movement that should have been started a long time ago, one that should be free of bias, prejudice, hatred, and scorn, one that provide instant solutions to poverty, disease, unemployment, racism, strife, war, and hardship.
Once we have begun to accept the idea of a globalized database that reflects certain acceptable constraint requirements in accordance with the effectiveness formula mentioned supra the world is bound to change for the better. We cannot help but to await the coming of this new dawn with enthusiasm and bated breath.
However, in the meantime our most urgent quest is to find ways and means to define, describe, explain, predict, and control behavior, both good, bad, and degrees between law-abiding and criminal acts, while applying the effectiveness formula for acceptable and unacceptable behavior and quality control diligently.
Here we are confronted with a formidable task of such complexity and extensive scope that even a super computer would fail in making sense of the factorial design and relationships that would be generated if a 20% sample of the world’s population is selected for analysis.
Let us now, just for our own benefit, take a cursory look at some of the variables and assumptions that may be considered for such an exercise. Let us begin by adopting a normal distribution pattern to be exploited. Very soon we shall discover that time and financial constraints dictate every procedural step we take’ whether we decide upon a normal distribution or any other approach,
25.0 A normal distribution of variables to analyze behavior
The trick is to put each respondent’s details on a dynamic speed-of-light-changing chronological distribution, the functions of which have first of all to be established as valid and reliable. Without further ado we know that this cannot be done because it takes time to gather, process, and clear each entry.
26.0
Genetic inherited patterns
We know much too little about these phenomenal variables in order to attempt any valid and reliable description, let alone any explanation, prediction, and control scenario. We are for example unsure whether the genetic strings are stable over time and whether they are not apt to drift along in the cells.
27.0 Environmental
experiences
Here again we are confronted with so many mysteries, biased opinions, and outright lies, that no credence ought to be attached to any version contributed by the respondent. Worst of all most of these so-called experiences are buried deeply in the mind or subconscious thoughts of the respondent. Most of them are impressions and not amenable to precise validation, although they form the basis of the respondent’s so-called genotype. Over some period of time the respondent seems to develop the capacity to alter the impact and role of any learning and conditioning experience considerably, sometimes to such an extent that they assume quite another form.
28.0
Crime
situations
The experiences
gained in the crime situation, both by the criminal and the victim alike, is a
subset of the environmental set, but treated as a separate set because the
creation of special relationships like those discussed supra. Many types of mechanisms like demand and supply; provocation; and Stockholm syndrome may be resorted to. Stockholm
syndrome occurs in situations of extreme stress,
bringing about an emotional discharge that turns the hate and resentment of the
victim towards a hostage taker to affection and even love, to such an extent
that the victim forthwith sides with the captor and helps the captor to
complete his mission. All in all the victims may contribute and add to the
constraints placed on the police force and the authorities who are standing by
to free the hostages. Here again we notice how difficult it becomes to identify
and attach a weight to the different variables that go into the equation.
29.0 The way ahead
From the briefing
supra, one may come to the conclusion that the social scientists – especially
the criminologists – have landed up in a cul-de-sac, unable to come up with any
plans and ideas to break the log-jam, or to resolve the problems mentioned and
spelled out above. However, they will be called upon by future generations to
explain their failed quest to have effectively described, explained, and
predicted the ebb and flow of ‘crime’ and suggested control measures to keep it
in check. Perhaps the few suggestions made above may enable some researcher to
come up with feasible solutions to the crime conundrum.
30.0 A parting note on looking
ahead
Thus far we have become aware of the glaring fact that life is riddled with dilemmas – some of them solvable and amenable to unraveling, but some, if not most, hard nuts to crack.
There will have to be a wake-up call for a realization that ‘I am because you are’ imbibes us with a clear understanding that every individual who has walked our earth, and this one here that sees the light of day now, or that one there who will be born tomorrow, is unique or alone of its kind and must be respected as such.
The desire of man to be the supreme leader of the world, despite the fact that the world has been slip-sliding into poverty, want and chaos, has escalated into a furious race between warring groups that do not hesitate to revert to terrorism and to the use and abuse of weapons of mass destruction to achieve the supreme authority.
No matter how we see and define the situation, the bottom line is that a considerable number of world leaders share the highly questionable view that the need for security and safety makes war on exceptional occasions an essential evil, the lesser one of two evils that confronts the world in our day and age. This, they say, must be of course the only option after the provocative action of the warring party has been translated into a reaction of valid self defence, if, and only if, ALL OTHER MEANS AND WAYS to defuse the situation have failed; and only resorted to until the original aggression started by the other party has been stopped or come to an end. Alternatively, the wronged party must rather put its case before the United Nations Assembly for adjudication and appropriate reactionary decisions.
My heartfelt wish is that the powers to be all over the world come to an undivided resolution to declare the third millennium A.D. the Millennium of the Child, embracing all the ramifications that may ensued with such an extensive and wide-reaching procedure, with gusto and resolve.
In the early eighties of the past century I coined a maxim which has since then become my second nature, to guide me towards achieving some headway towards leaving this earth a better place as the one I happened to have experienced, up till now, a world teeming with unresolved dilemmas.
However the powers that be strive to resolve their dilemmas, and wherever the number game is being played and regulated the world over, in my book the
single individual is still the Number One choice. I do believe that the
ultimate realization of the goal of peace and tranquility
the world hopes to achieve, is predicated on
our belief that ‘I am because you are’
and on its valid counterpart
‘you are because I am.’
References
- Bronowski, pp. 96-7
- A concept coined by the author in his unpublished manuscript ‘I am because you are – an introduction to the science of security’. 2006
- Sarah Tulloch: pp 1835-1836
- Jacob van der Westhuizen 2006. Excerpts
from unpublished manuscript
‘I am because you are ‘ – the author’s
maxim coined in the early eighties
of the last century).
- Sarah Tulloch, p.1835
- Josef Joffe in Time January 29, 2007. ‘Those gloating dismal scientists.’
Vol. 169, No 5, p. 60
- Jacob van der Westhuizen,
ibid. p.136
- Ligthelm, Andrė of the Bureau of Market Research of the University of
Stellenbosch.as quoted by Johann van Tonder: ‘Onwettige derde ekonomie
floreer’ – (Illegal third economy flourishes). Rapportsake. February 12,
2006. p. 1.
9. Jacob van der Westhuizen, ibid. pp. 28-131
10. Merton(9 (in
Giallombardo, R.- editor.1966. Juvenile
Delinquency – a book
of readings: Wiley & Sons:
11. Interview conducted and recorded in Time, September 18, 2006 by
Time’s Jessica Carsen with the Human
Rights Lawyer, Gareth Pearce, p.19
12. Jacob van der
Westhuizen, ibid.
13. Toon, Ernest R. and George L. Ellis.
1973. Foundations of chemistry. New
14. Sarah Tulloch, p. 594
15. ibid.
16. ibid.
17. Editorial Staff of the Reader’s
Digest, pp. 141-2
18. Sarah Tulloch, p. 594
19. Hunt, 1970:714
20. Le
Roux in Du Preez, p. 228 et seq.
21. Klaus
Schwab, founder and executive chairman of the WEF (World Economic Forum 2007) highlights some of
these challenges the world is facing: World Economic Forum. Announcements made in the media and
on the Internet about global issues of maximal global concern.
22. Jacob van der Westhuizen, pp.294-6
2006
23. Robinson quoted by Seidemann, May 7,
2007 in Time Vol 169 No 19. p.
64
24.
Jacob
vd Westhuizen, ch. 10
25.
ibid.,
pp. 119-121
26.
Hiemstra V.G. and H.L.Gonin, 1990. Trilingual Legal Dictionary . Juta & Kie Beperk:
27. Jacob van der Westhuizen, pp. 122
28.
Bromberg, W. 1965. Crime
and the mind. MacMillan:
29.
Eysenck, H.J. 1964. Crime
and Personality. Routledge and Kegan Paul. :
30. Jacob
van der Westhuizen, p. 123
31. Jacob
van der Westhuizen, pp. 186-188
32. ibid.
33. ibid.
34. ibid.
35. Cavan, 1962, p.45
36. ibid.
37. 1962,
p.45
38. Vold, 1958, pp. 282-304
39. Jacob
van der Westhuizen, chapters 21-22
40.
41. Jacob van
der Westhuizen, 2006. chapter 22.
42. The
author defined, developed, and refined the theory in close collaboration with
his son, Dr Jakes van der Westhuizen, an orthopaedic specialist of
Bibliography
Bronowski, J. 1968. The common sense of science. Penguin
Books
Cavan, Ruth. 1962. Criminology. Thomas Y Crowell:
Eysenck,
H.J. 1964. Crime and Personality.
Routledge & Kegan Paul:
Giancoli, Douglas C. 1988. Physics for scientists and engineers. Prentice-Hall:
Hunt, PMA. 1970. South African Criminal Law and Proceddure.
Juta:
Klaus Schwab, founder and
executive chairman of the WEF (World Economic Forum). 2007. World
Economic Forum. Announcements made in the media and on the Internet about
global issues of maximal global concern.
Le Roux, D. in Du Preez -editor,
1991. Security Forum. Butterworhs:
Ligthelm, Andrė as quoted by Johann van Tonder: ‘Onwettige derde ekonomie
floreer ‘(Illegal third economy flourishes) Rapport Sake: February 12, 2006. p. 1.
Merton (in Giallombardo, R.-
editor.1966. Juvenile Delinquency – a
book of readings: Wiley & Sons:
Pearce, Gareth, Human Rights Lawyer,
interviewed by Jessica Carsen of Time,
September 18, 2006.
Reader’s Digest Editorial Staff:
1970. Use the right word- modern guide to
synonyms and related words. The reader’s Digest:
Simon Robinson. May 7, 2007. ‘A
World Divided.’ In Time Vol. 169,
No19, p.64.
Toon, Ernest
R. and George L. Ellis. 1973. Foundations
of chemistry. Holt, Rinehart and
Winston:
Tulloch,
Sara (ed). 1993. Complete Word Finder.
Reader’s Digest:
Vold, George B. 1958. Theoretical Criminology.
Van der Westhuizen, Jacob. 2006. Excerpt
from unpublished manuscript ‘I am because you are – an introduction to the
science of security’.
Van
der Westhuizen, 1982. Jacob (editor
& co-writer). Crimes of violence in
Van der Westhuizen, Jacob. An introduction to criminological research.
Van
der Westhuizen, Jacob and Hennie Oosthuizen. Prediction of parole
failure and maladjustment.
Van
der Westhuizen, Jacob in Du Preez, G.T. (ed.) Security Forum.
Butterworhs:
Van
der Westhuizen, Jacob. Security
management.
Africa:
Van der Westhuizen, Jacob. (ed & co-writer) Forensic Criminalistics.
Butterworhs;
Van der Westhuizen, Jacob. ‘One more time:
views on Aristotle’s philosophy
and intercultural philosophy’, Phronimon - Journal of the
South
African Society for Greek Philosophy
and the Humanities. Vol. 6(1)
2005: pp. 71-79
Van der Westhuizen, Jakes. 2007. (esteemed
contributor to defining, de-
scribing, and developing the constraint theory, showcased on pp. 50-52)
Vold,
George B. Theoretical Criminology.
Welkowitz,
Joan, Robert B. Ewen & Jacob Cohen. Introductory
Statistics
for the Behavioral Sciences. Harcourt Brace Jovanovich: New
Wike, Edward L. Numbers – a primer of data analysis. Charles E. Merrill:
Young, Pauline V. Scientific Social Surveys and Research. Prentice-Hall:
NJ. 1963
[ BWW Society Home Page ]
© 2007 The Bibliotheque: World Wide Society